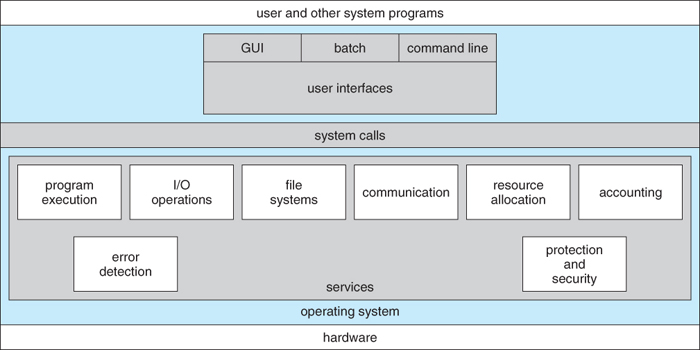
- Process management
- Memory management
- File management
- I/O system management
- Secondary-storage management
- Networking
- Protection
- User interface
- Command line interface (CLI)
- Graphical user interface (GUI)
- Batch
- Program execution
- The system must be able to load a program into memory and to run that program, end execution, either normally or abnormally (indicating error)
- I/O operations
- A running program may require I/O, which may involve a file or an I/O device
- File-system manipulation
- Programs need to read and write files and directories, create and delete them, search them, list file Information, permission management.
- Communication
- Processes may exchange information, on the same computer or between computers over a network
- shared memory or through message passing (packets moved by the OS)
- Error detection
- OS needs to be constantly aware of possible errors
- May occur in the CPU/memory hardware, in I/O devices, in user program
- For each type of error, OS should take the appropriate action to ensure correct and consistent computing
- Debugging facilities can greatly enhance the user�s and programmer�s abilities to efficiently use the system
- Protection and security
- The owners of information stored in a multiuser or
networked computer system may want to control use of that information,
concurrent processes should not interfere with each other
- Protection involves ensuring that all access to system resources is controlled
- Security of the system from outsiders requires user authentication, extends to defending external I/O devices from invalid access attempts
- The owners of information stored in a multiuser or
networked computer system may want to control use of that information,
concurrent processes should not interfere with each other
- Resource allocation
- When multiple users or multiple jobs running concurrently, resources must be allocated to each of them
- Many types of resources
- CPU cycles, main memory, file storage, I/O devices
- Accounting
- keep track of which users use how much and what kinds of computer resources
- Command line interface (CLI)
- CLI or command interpreter allows direct command entry
- Sometimes implemented in kernel, sometimes by systems program
- Sometimes multiple flavors implemented – shells
- Primarily fetches a command from user and executes it (fork/execv)
- Sometimes commands built-in, sometimes just names of programs
- If the latter, adding new features doesn’t require shell modification
- Graphical user interface (GUI)
- User-friendly desktop metaphor interface – PCs, Tablets?
- Usually mouse, keyboard, and monitor
- Icons represent files, programs, actions, etc
- Various mouse buttons over objects in the interface cause various actions (provide information, options, execute function, open directory (known as a folder)
- Invented at Xerox PARC – not Apple
- User-friendly desktop metaphor interface – PCs, Tablets?
- Many systems now include both CLI and GUI interfaces
- Microsoft Windows is GUI with CLI command shell
- Apple Mac OS X is Aqua GUI interface with UNIX kernel underneath and shells available
- Unix and Linux have CLI with optional GUI interfaces (CDE, KDE, GNOME)
- Syscalls is the interface for User programs to talk to the OS
- Programming interface to the services provided by the OS
- Typically written in a high-level language (C or C++)
- OS resources are mostly accessed by programs via a high-level Application Program Interface (API) rather than direct syscall use
- Three most common APIs (often in form of libraries)
- Win32 API for Windows
- POSIX API for POSIX-based systems (UNIX, Linux, Mac OS X)
- Java API for the Java virtual machine (JVM)
- Why use APIs rather than system calls?
- easier, more portable
- Parameter passing
- Three general methods used to pass parameters to the OS
- Register
- Simply pass the parameters in registers
- In some cases, may be more parameters than registers
- Memory block
- Parameters stored in a block, or table, in memory, and address of block passed as a parameter in a register
- This approach taken by Linux and Solaris
- Stack
- Parameters placed, or pushed, onto the stack by the program and popped off the stack by the operating system
- Note: Block and stack methods do not limit the number or length of parameters being passed
- Register
- Three general methods used to pass parameters to the OS
- Five categories of system calls
- Process control
- create process, terminate process
- end, abort
- load, execute
- get process attributes, set process attributes
- wait for time
- wait event, signal event
- allocate and free memory
- Dump memory if error
- Debugger for determining bugs, single step execution
- Locks for managing access to shared data between processes
- File management
- create file, delete file
- open, close file
- read, write, reposition
- get and set file attributes
- Device management
- request device, release device
- read, write, reposition
- get device attributes, set device attributes
- logically attach or detach devices
- Information maintenance
- get time or date, set time or date
- get system data, set system data
- get and set process, file, or device attributes
- Communications
- create, delete communication connection
- send, receive messages if message passing model to
host name or process name
- From client to server
- Shared-memory model create and gain access to memory regions
- transfer status information
- attach and detach remote devices
- Protection
- Control access to resources
- Get and set permissions
- Allow and deny user access
- Not one of the 5 major
- Examples
- Message passing model
- Information is exchanged through inter-process communication facility provided by OS.
- Shared memory model
- Processes use map memory system calls to gain access to regions of memory owned by other processes.
- System programs provide a convenient environment for
program development and execution. They can be divided
into:
- File manipulation
- Status information
- File modification
- Programming language support
- Program loading and execution
- Communications
- Application programs
- Most users’ view of the operation system is defined by system programs, not the actual system calls
- Provide a convenient environment for program development and execution
- Some of them are simply user interfaces to system calls; others are considerably more complex
- File management - Create, delete, copy, rename, print, dump, list, and generally manipulate files and directories
- Status information
- System info - date, time, free memory, disk space, number of users
- Detailed performance, logging, and debugging information
- Typically, these programs format and print the output to the terminal or other output devices
- Some systems (UNIX) uses text files (.conf) to store configuration
- Some systems (Windows) implement a registry - used to store and
retrieve configuration information
- Limitations – Requires dedicated uninstaller; difficult to move settings to another machine; corrupted registry requires system reinstallation
- File modification
- Text editors to create and modify files
- Special commands to search contents of files or perform transformations of the text
- Programming-language support - Compilers, assemblers, debuggers and interpreters sometimes provided
- Program loading and execution- Absolute loaders, relocatable loaders, linkage editors, and overlay-loaders, debugging systems for higher-level and machine language
- Communications - Provide the mechanism for creating virtual
connections among processes, users, and computer systems
- Allow users to send messages to one another’s screens, browse web pages, send electronic-mail messages, log in remotely, transfer files from one machine to another
- Background Services
- Launch at boot time
- Some for system startup, then terminate
- Some from system boot to shutdown
- Provide facilities like disk checking, process scheduling, error logging, printing
- Run in user context not kernel context
- Known as services, subsystems, daemons
- Launch at boot time
- Application programs
- Don’t pertain to system
- Run by users
- Not typically considered part of OS
- Launched by command line, mouse click, finger poke
- Design and Implementation of OS not solvable, but some approaches have proven successful (based on practice)
- Design
- Internal structure of different Operating Systems can vary widely
- Start the design by defining goals and specifications
- Affected by choice of hardware, type of system
- User goals and System goals
- User goals – operating system should be convenient to use, easy to learn, reliable, safe, and fast
- System goals – operating system should be easy to design, implement, and maintain, as well as flexible, reliable, error-free, and efficient
- Mechanisms and policies
- Important principle in system design to separate
- Policy: What will be done?
- Mechanism: How to do it?
- Important principle in system design to separate
- Mechanisms determine how to do something, policies decide what will be done
- The separation of policy from mechanism is a very important principle, it allows maximum flexibility if policy decisions are to be changed later (example – timer)
- Specifying and designing an OS is highly creative task of software engineering
- Implementation
- After an OS is designed, it needs to be implemented
- Much variation
- Early OSes in assembly language
- Then system programming languages like Algol, PL/1
- Now C, C++ (e.g., Linux is mostly in C)
- Actually usually a mix of languages
- Lowest levels in assembly
- Main body in C
- Systems programs in C, C++, scripting languages like PERL, Python, shell scripts
- High-level language easier to port to other hardware, but slower
- Emulation can allow an OS to run on non-native hardware
- Organization of OS components to specify the privilege with which each component executes.
- Four structures
- Monolithic
- All components contained in the kernel
- Layered
- Top-down approach to separate the functionality and features into components.
- The operating system is divided into a number of layers (levels), each built on top of lower layers. The bottom layer (layer 0), is the hardware; the highest (layer N) is the user interface.
- With modularity, layers are selected such that each uses functions (operations) and services of only lower-level layers
- Design and implementation of OS get simplified in the layered approach.
- Microkernel
- Only essential components included in the kernel
- Moves as much from the kernel into user space
- Kernel maintains the minimum generic OS functions
- Mach example of microkernel developed by CMU
- Mac OS X kernel (Darwin) partly based on Mach
- Communication takes place between user modules using message passing
- Benefits:
- Easier to extend a microkernel
- Easier to port the operating system to new architectures
- More reliable (less code is running in kernel mode)
- More secure
- Detriments:
- Performance overhead of user space to kernel space communication
- Modules
- Object-oriented structure
- Monolithic
- Tanenbaum-Torvalds Debate
- 1992, Usernet discussion group comp.os.minix
- Andrew S. Tanenbaum – Minix
- Microkernel is better for portability
- Linux is too closely tied to expensive Intel 386
- x86 processors will be superseded
- Linux, as a monolithic kernel, is “a giant step back into 1970s”
- Linus Torvalds – Linux
- Linux API is more portable and simpler
- Choosing x86 is explicit design goal, rather than a design flaw
- Building for cheap hardware will have portability problems
- A virtual machine takes the layered approach to its logical conclusion. It treats hardware and OS kernel as all hardware.
- A VM provides an interface to the underlying bare hardware.
- The operating system host creates the illusion that a process has its own processor and (virtual memory).
- Each guest provided with a (virtual) copy of underlying computer.
- Virtual Machines run on the top of any OS
- VMware and the Java Virtual machine
- VM is the basic building block of cloud computing systems
- History
- First appeared commercially in IBM mainframes in 1972
- Fundamentally, multiple execution environments (different operating systems) can share the same hardware
- Advantages
- Main Benefits
- Sharing – Hardware resource can be better utilized
- Protection – Guest VMs are protected from each other
- Consolidation – Low-resource use systems are clustered one one
- Other benefits
- Guest VMs can communicate with each other and to outside
- Useful for development, debugging, experiments, testing (Sandbox)
- Main Benefits
- “Open Virtual Machine Format”, standard format of virtual machines, allows a VM to run within many different virtual machine (host) platforms VM is the basic building block of cloud computing systems
- Implementation
- Difficult to implement
- Typically runs in user mode, creates virtual user mode and virtual kernel mode
- Timing can be an issue – slower than real machine
- Hardware support provided (AMD, Intel)
- More support ! better virtualization
- i.e. Intel VT, AMD provides “host” and “guest” modes
- Debugging is finding and fixing errors, or bugs
- OS generate log files containing error information
- Failure of an application can generate core dump file capturing memory of the process
- Operating system failure can generate crash dump file containing kernel memory
- Beyond crashes, performance tuning can optimize system
performance
- Sometimes using trace listings of activities, recorded for analysis
- Profiling is periodic sampling of instruction pointer to look for statistical trends
Kernighan�s Law
Debugging is twice as hard as writing the code in the first place. Therefore,
if you write the code as cleverly as possible, you are, by definition, not
smart enough to debug it.
- Generation
- Operating systems are designed to run on any of a class of machines; the system must be configured for each specific computer site
- SYSGEN program obtains information concerning the specific
configuration of the hardware system
- Used to build system-specific compiled kernel or system-tuned
- Can general more efficient code than one general kernel
- Booting
- starting a computer by loading the kernel
- Bootstrap program
- code stored in ROM that is able to locate the kernel, load it into memory, and start its execution
- System Boot
- When power initialized on system, execution starts at a fixed
memory location
- Firmware ROM used to hold initial boot code
- Operating system must be made available to hardware so
hardware can start it
- Small piece of code – bootstrap loader, stored in ROM or EEPROM locates the kernel, loads it into memory, and starts it
- Sometimes two-step process where boot block at fixed location loaded by ROM code, which loads bootstrap loader from disk
- Common bootstrap loader, GRUB, allows selection of kernel from multiple disks, versions, kernel options (e.g., Windows/Linux)
- Kernel loads and system is then running
- When power initialized on system, execution starts at a fixed
memory location
- OS provides a number of services.
- Lowest level: system calls allow a running program to make direct requests from OS.
- Higher level: command interpreter or shell provides a mechanism to issue a request without writing a program.
- System calls provide basic functions, such as process control, I/O requests, status control, communication.
- Design becomes flexible with separation of policy and mechanism.
- OS is now written in a high-level language.
- A layered approach or microkernel results in modularity.
- Virtual-machine concept treats both the OS kernel and hardware as though they were all hardware
- SYMGEN creates an OS for a particular machine configuration.