diff --git a/.github/ISSUE_TEMPLATE/bug_report.md b/.github/ISSUE_TEMPLATE/bug_report.md
index 4e89b19..6841ea3 100644
--- a/.github/ISSUE_TEMPLATE/bug_report.md
+++ b/.github/ISSUE_TEMPLATE/bug_report.md
@@ -10,6 +10,9 @@ assignees: ''
**Describe the bug**
A clear and concise description of what the bug is.
+**Powerpipe version (`powerpipe -v`)**
+Example: v0.3.0
+
**Steampipe version (`steampipe -v`)**
Example: v0.3.0
diff --git a/.github/ISSUE_TEMPLATE/config.yml b/.github/ISSUE_TEMPLATE/config.yml
index bef7650..04798f2 100644
--- a/.github/ISSUE_TEMPLATE/config.yml
+++ b/.github/ISSUE_TEMPLATE/config.yml
@@ -3,6 +3,9 @@ contact_links:
- name: Questions
url: https://turbot.com/community/join
about: GitHub issues in this repository are only intended for bug reports and feature requests. Other issues will be closed. Please ask and answer questions through the Steampipe Slack community.
+ - name: Powerpipe CLI Bug Reports and Feature Requests
+ url: https://github.com/turbot/powerpipe/issues/new/choose
+ about: Powerpipe CLI has its own codebase. Bug reports and feature requests for those pieces of functionality should be directed to that repository.
- name: Steampipe CLI Bug Reports and Feature Requests
url: https://github.com/turbot/steampipe/issues/new/choose
about: Steampipe CLI has its own codebase. Bug reports and feature requests for those pieces of functionality should be directed to that repository.
\ No newline at end of file
diff --git a/.gitignore b/.gitignore
index 0e169d5..4630886 100644
--- a/.gitignore
+++ b/.gitignore
@@ -12,8 +12,13 @@
*.spvars
*.auto.spvars
+# Powerpipe variable files
+*.ppvars
+*.auto.ppvars
+
# Steampipe mod dependencies
.steampipe
+.powerpipe
# Cache json files
*.cache.json
diff --git a/CHANGELOG.md b/CHANGELOG.md
index e9e8690..133ebf9 100644
--- a/CHANGELOG.md
+++ b/CHANGELOG.md
@@ -1,3 +1,16 @@
+## v0.11 [2024-04-06]
+
+_Powerpipe_
+
+[Powerpipe](https://powerpipe.io) is now the preferred way to run this mod! [Migrating from Steampipe →](https://powerpipe.io/blog/migrating-from-steampipe)
+
+All v0.x versions of this mod will work in both Steampipe and Powerpipe, but v1.0.0 onwards will be in Powerpipe format only.
+
+_Enhancements_
+
+- Focus documentation on Powerpipe commands.
+- Show how to combine Powerpipe mods with Steampipe plugins.
+
## v0.10 [2024-01-12]
_Bug fixes_
diff --git a/README.md b/README.md
index 2dc249b..35cb9c2 100644
--- a/README.md
+++ b/README.md
@@ -1,133 +1,138 @@
-# AWS Well-Architected Mod for Steampipe
+# AWS Well-Architected Mod for Powerpipe
+
+> [!IMPORTANT]
+> [Powerpipe](https://powerpipe.io) is now the preferred way to run this mod! [Migrating from Steampipe →](https://powerpipe.io/blog/migrating-from-steampipe)
+>
+> All v0.x versions of this mod will work in both Steampipe and Powerpipe, but v1.0.0 onwards will be in Powerpipe format only.
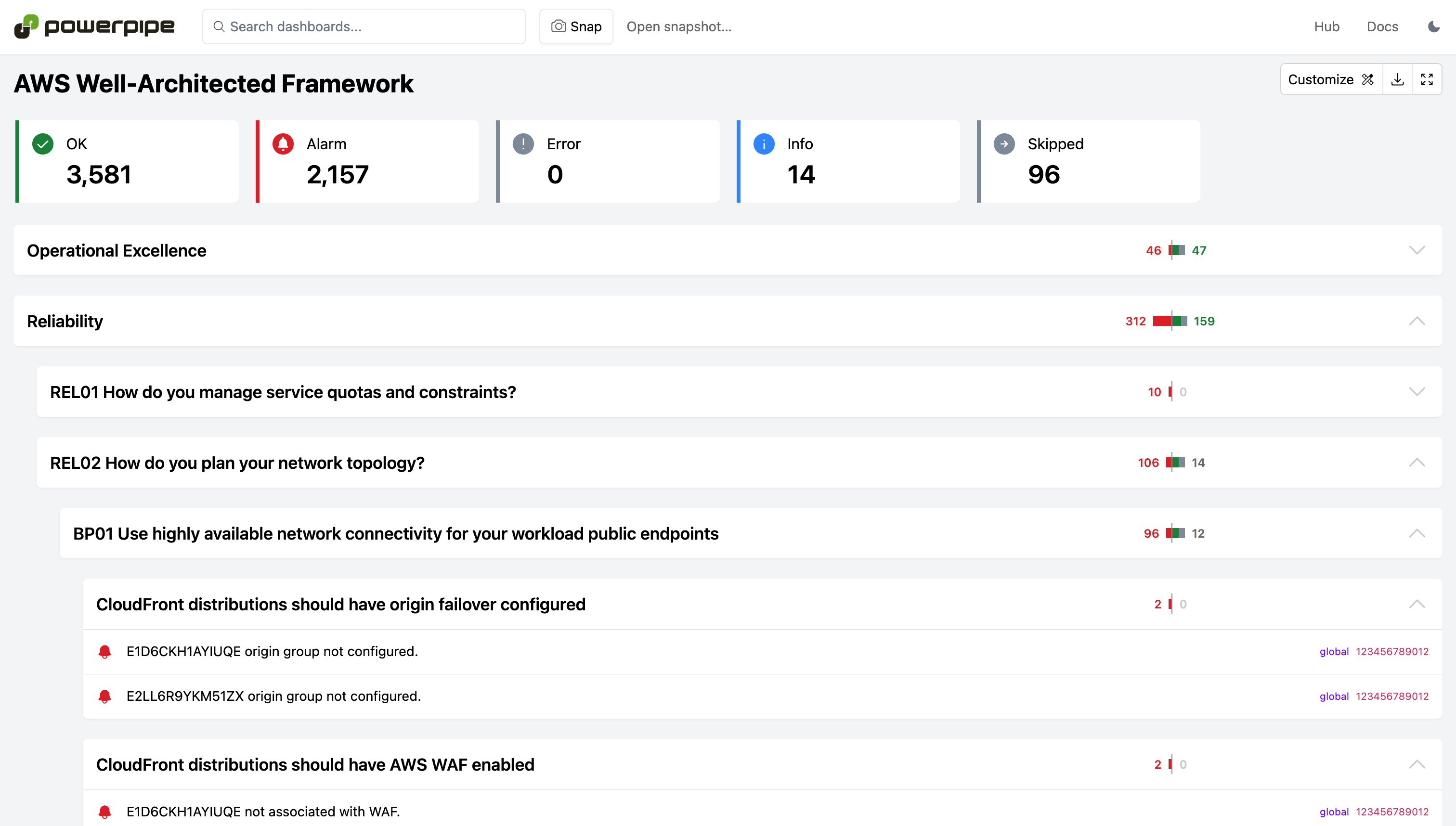
200+ checks covering AWS Well-Architected Framework defined best practices across all AWS regions.
Run checks in a dashboard:
-
+
-Includes support for:
-* [Reliability Pillar](https://hub.steampipe.io/mods/turbot/aws_well_architected/controls/benchmark.reliability)
-* [Security Pillar](https://hub.steampipe.io/mods/turbot/aws_well_architected/controls/benchmark.security)
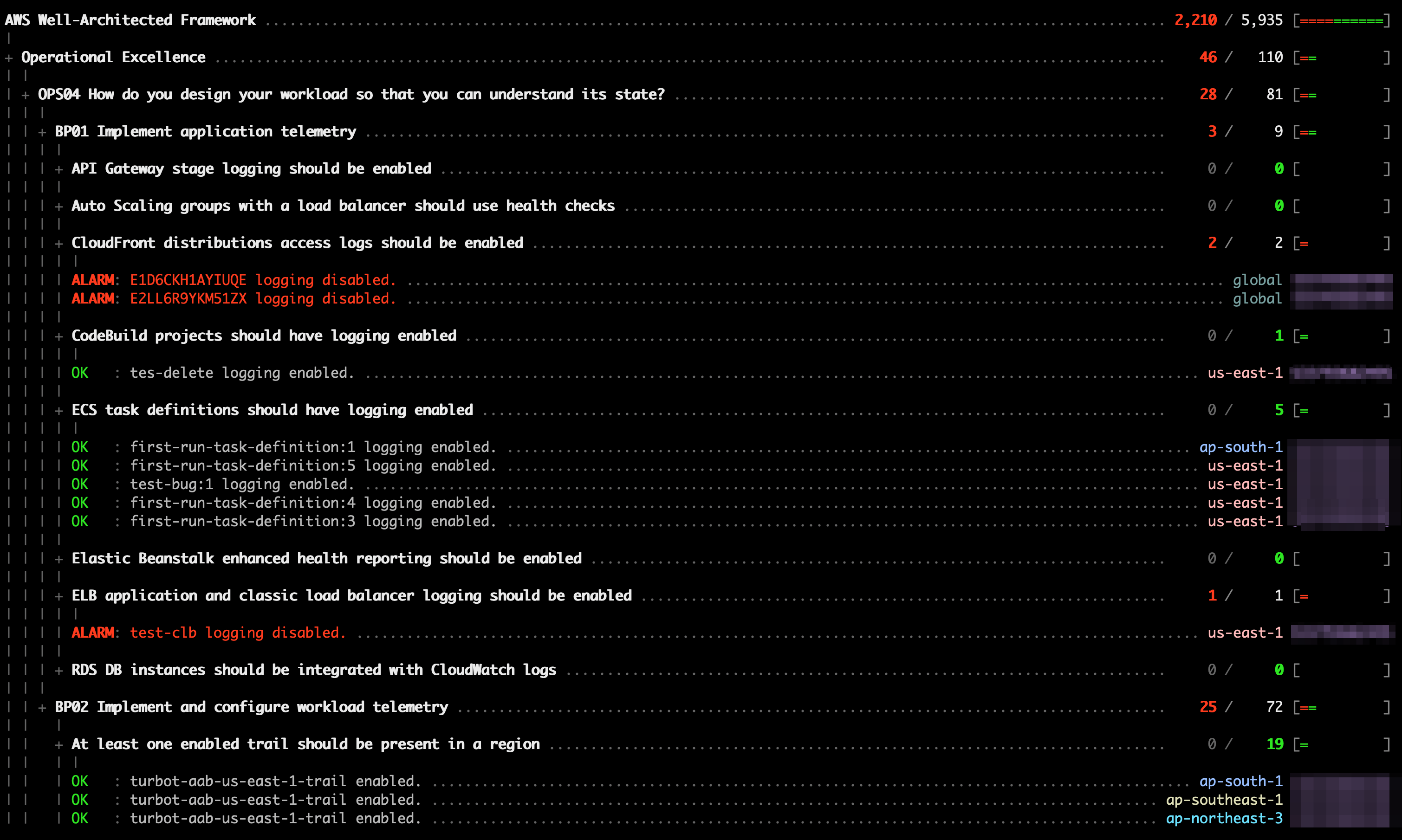
+Or in a terminal:
+
-## Getting started
+## Getting Started
### Installation
-Download and install Steampipe (https://steampipe.io/downloads). Or use Brew:
+Install Powerpipe (https://powerpipe.io/downloads), or use Brew:
```sh
-brew tap turbot/tap
-brew install steampipe
+brew install turbot/tap/powerpipe
```
-Install the AWS plugin with [Steampipe](https://steampipe.io):
+This mod also requires [Steampipe](https://steampipe.io) with the [AWS plugin](https://hub.steampipe.io/plugins/turbot/aws) as the data source. Install Steampipe (https://steampipe.io/downloads), or use Brew:
```sh
+brew install turbot/tap/steampipe
steampipe plugin install aws
```
-Clone:
-
-```sh
-git clone https://github.com/turbot/steampipe-mod-aws-well-architected.git
-cd steampipe-mod-aws-well-architected
-```
+Steampipe will automatically use your default AWS credentials. Optionally, you can [setup multiple accounts](https://hub.steampipe.io/plugins/turbot/aws#multi-account-connections) or [customize AWS credentials](https://hub.steampipe.io/plugins/turbot/aws#configuring-aws-credentials).
-Install mod dependencies:
+Finally, install the mod:
```sh
-steampipe mod install
+mkdir dashboards
+cd dashboards
+powerpipe mod init
+powerpipe mod install github.com/turbot/steampipe-mod-aws-well-architected
```
-### Usage
+### Browsing Dashboards
-Before running any benchmarks, it's recommended to generate your AWS credential report:
+Start Steampipe as the data source:
```sh
-aws iam generate-credential-report
+steampipe service start
```
-Start your dashboard server to get started:
+Start the dashboard server:
```sh
-steampipe dashboard
+powerpipe server
```
-By default, the dashboard interface will then be launched in a new browser
-window at http://localhost:9194. From here, you can run benchmarks by
-selecting one or searching for a specific one.
+Browse and view your dashboards at **http://localhost:9033**.
+
+### Running Checks in Your Terminal
Instead of running benchmarks in a dashboard, you can also run them within your
-terminal with the `steampipe check` command:
+terminal with the `powerpipe benchmark` command:
-Run all benchmarks:
+List available benchmarks:
```sh
-steampipe check all
+powerpipe benchmark list
```
-Run a single benchmark:
+Run a benchmark:
```sh
-steampipe check benchmark.well_architected_framework
+powerpipe benchmark run well_architected_framework
```
Run a benchmark for a specific pillar:
```sh
-steampipe check benchmark.well_architected_framework_security
+powerpipe benchmark run well_architected_framework_security
```
Run a benchmark for a specific question:
```sh
-steampipe check benchmark.well_architected_framework_sec01
+powerpipe benchmark run well_architected_framework_sec01
```
Run a benchmark for a specific best practice:
```sh
-steampipe check benchmark.well_architected_framework_sec01_bp01
+powerpipe benchmark run well_architected_framework_sec01_bp01
```
Different output formats are also available, for more information please see
-[Output Formats](https://steampipe.io/docs/reference/cli/check#output-formats).
-
-### Credentials
+[Output Formats](https://powerpipe.io/docs/reference/cli/benchmark#output-formats).
-This mod uses the credentials configured in the [Steampipe AWS plugin](https://hub.steampipe.io/plugins/turbot/aws).
+### Common and Tag Dimensions
-### Configuration
+The benchmark queries use common properties (like `account_id`, `connection_name` and `region`) and tags that are defined in the dependent [AWS Compliance mod](https://github.com/turbot/steampipe-mod-aws-compliance) These properties can be executed in the following ways:
-No extra configuration is required.
+It's easiest to setup your vars file, starting with the sample:
-### Common and Tag Dimensions
+```sh
+cp steampipe.spvars.example steampipe.spvars
+vi steampipe.spvars
+```
-The benchmark queries use common properties (like `account_id`, `connection_name` and `region`) and tags that are defined in the dependent [AWS Compliance mod](https://github.com/turbot/steampipe-mod-aws-compliance). These properties can be executed in the following ways:
+Alternatively you can pass variables on the command line:
-- Copy and rename the `steampipe.spvars.example` file to `steampipe.spvars`, and then modify the variable values inside that file
+```sh
+powerpipe benchmark run well_architected_framework_security --var 'common_dimensions=["account_id", "connection_name", "region"]'
+```
-- Pass in a value on the command line:
+Or through environment variables:
- ```shell
- steampipe check benchmark.well_architected_framework_security --var 'common_dimensions=["account_id", "connection_name", "region"]'
- ```
+```sh
+export PP_VAR_common_dimensions='["account_id", "connection_name", "region"]'
+export PP_VAR_tag_dimensions='["Environment", "Owner"]'
+powerpipe benchmark run well_architected_framework_security
+```
- ```shell
- steampipe check benchmark.well_architected_framework_security --var 'tag_dimensions=["Environment", "Owner"]'
- ```
+## Open Source & Contributing
-## Contributing
+This repository is published under the [Apache 2.0 license](https://www.apache.org/licenses/LICENSE-2.0). Please see our [code of conduct](https://github.com/turbot/.github/blob/main/CODE_OF_CONDUCT.md). We look forward to collaborating with you!
-If you have an idea for additional controls or just want to help maintain and extend this mod ([or others](https://github.com/topics/steampipe-mod)) we would love you to join the community and start contributing.
+[Steampipe](https://steampipe.io) and [Powerpipe](https://powerpipe.io) are products produced from this open source software, exclusively by [Turbot HQ, Inc](https://turbot.com). They are distributed under our commercial terms. Others are allowed to make their own distribution of the software, but cannot use any of the Turbot trademarks, cloud services, etc. You can learn more in our [Open Source FAQ](https://turbot.com/open-source).
-- **[Join #steampipe on Slack →](https://turbot.com/community/join)** and hang out with other Mod developers.
+## Get Involved
-Please see the [contribution guidelines](https://github.com/turbot/steampipe/blob/main/CONTRIBUTING.md) and our [code of conduct](https://github.com/turbot/steampipe/blob/main/CODE_OF_CONDUCT.md). All contributions are subject to the [Apache 2.0 open source license](https://github.com/turbot/steampipe-mod-aws-well-architected/blob/main/LICENSE).
+**[Join #powerpipe on Slack →](https://turbot.com/community/join)**
-Want to help but not sure where to start? Pick up one of the `help wanted` issues:
+Want to help but don't know where to start? Pick up one of the `help wanted` issues:
-- [Steampipe](https://github.com/turbot/steampipe/labels/help%20wanted)
+- [Powerpipe](https://github.com/turbot/powerpipe/labels/help%20wanted)
- [AWS Well-Architected Mod](https://github.com/turbot/steampipe-mod-aws-well-architected/labels/help%20wanted)
## Credits
diff --git a/docs/aws_well_architected_console.png b/docs/aws_well_architected_console.png
new file mode 100644
index 0000000..a51d1ee
Binary files /dev/null and b/docs/aws_well_architected_console.png differ
diff --git a/docs/aws_well_architected_dashboard.png b/docs/aws_well_architected_dashboard.png
deleted file mode 100644
index f6a473d..0000000
Binary files a/docs/aws_well_architected_dashboard.png and /dev/null differ
diff --git a/docs/aws_well_architected_reliability_dashboard.png b/docs/aws_well_architected_reliability_dashboard.png
index e22667b..be209dd 100644
Binary files a/docs/aws_well_architected_reliability_dashboard.png and b/docs/aws_well_architected_reliability_dashboard.png differ
diff --git a/docs/aws_well_architected_security_dashboard.png b/docs/aws_well_architected_security_dashboard.png
deleted file mode 100644
index 9b3914b..0000000
Binary files a/docs/aws_well_architected_security_dashboard.png and /dev/null differ
diff --git a/docs/aws_well_architected_workload_risks_report.png b/docs/aws_well_architected_workload_risks_report.png
new file mode 100644
index 0000000..f3b8a6c
Binary files /dev/null and b/docs/aws_well_architected_workload_risks_report.png differ
diff --git a/docs/index.md b/docs/index.md
index 74a62d7..88e072b 100644
--- a/docs/index.md
+++ b/docs/index.md
@@ -1,147 +1,134 @@
----
-repository: "https://github.com/turbot/steampipe-mod-aws-well-architected"
----
-
# AWS Well-Architected Mod
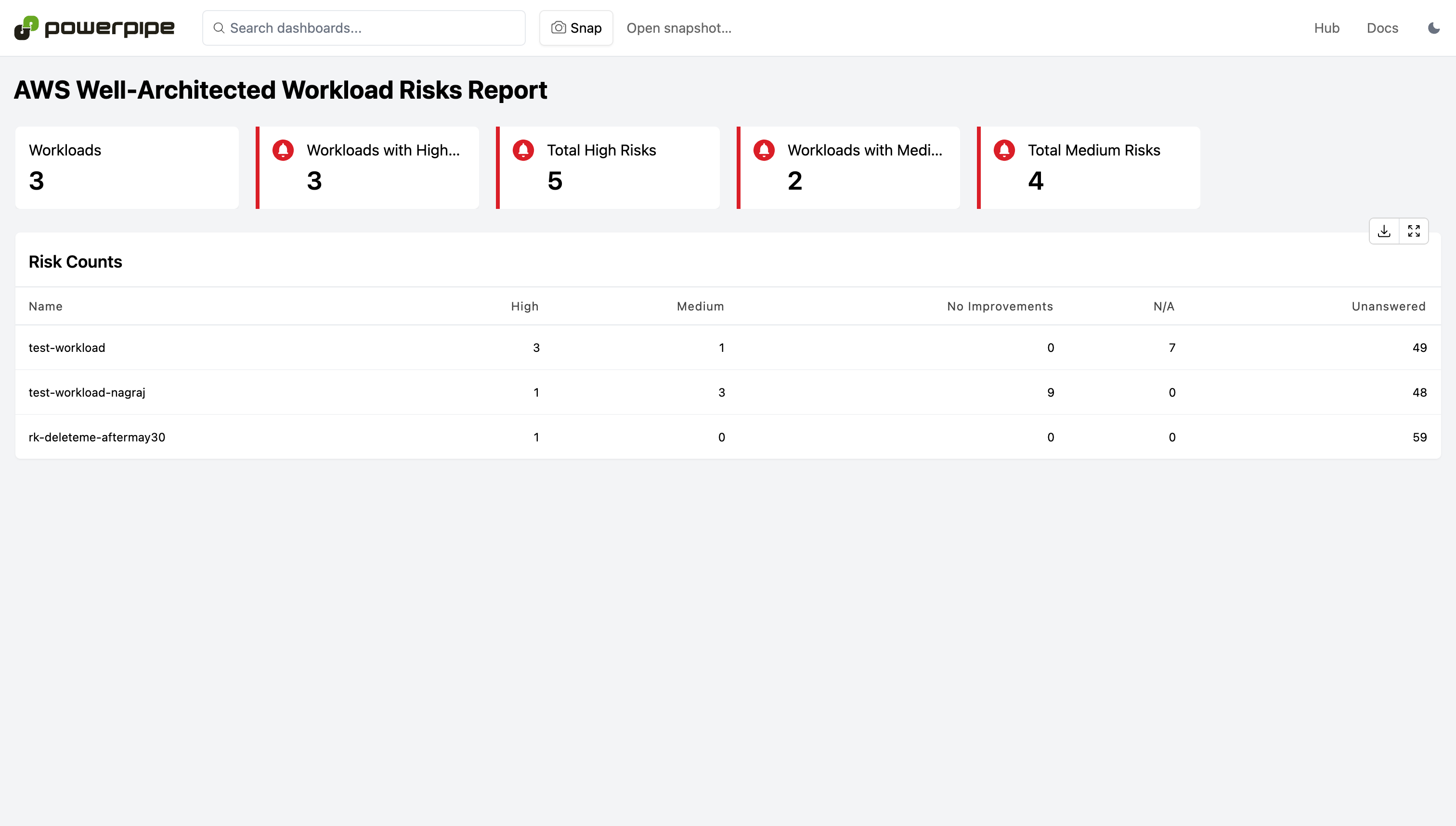
Run controls across all of your AWS accounts to check if they are following AWS Well-Architected Framework best practices.
- +
+ +
+
 -
- -
-## References
-
-[AWS](https://aws.amazon.com/) provides on-demand cloud computing platforms and APIs to authenticated customers on a metered pay-as-you-go basis.
-
-[AWS Well-Architected](https://aws.amazon.com/architecture/well-architected/) helps cloud architects build secure, high-performing, resilient, and efficient infrastructure for a variety of applications and workloads.
-
-[Steampipe](https://steampipe.io) is an open source CLI to instantly query cloud APIs using SQL.
-
-[Steampipe Mods](https://steampipe.io/docs/reference/mod-resources#mod) are collections of `named queries`, and codified `controls` that can be used to test current configuration of your cloud resources against a desired configuration.
## Documentation
-- **[Benchmarks and controls →](https://hub.steampipe.io/mods/turbot/aws_well_architected/controls)**
-- **[Named queries →](https://hub.steampipe.io/mods/turbot/aws_well_architected/queries)**
+- **[Benchmarks and controls →](https://hub.powerpipe.io/mods/turbot/aws_well_architected/controls)**
+- **[Named queries →](https://hub.powerpipe.io/mods/turbot/aws_well_architected/queries)**
-## Getting started
+## Getting Started
### Installation
-Download and install Steampipe (https://steampipe.io/downloads). Or use Brew:
+Install Powerpipe (https://powerpipe.io/downloads), or use Brew:
```sh
-brew tap turbot/tap
-brew install steampipe
+brew install turbot/tap/powerpipe
```
-Install the AWS plugin with [Steampipe](https://steampipe.io):
+This mod also requires [Steampipe](https://steampipe.io) with the [AWS plugin](https://hub.steampipe.io/plugins/turbot/aws) as the data source. Install Steampipe (https://steampipe.io/downloads), or use Brew:
```sh
+brew install turbot/tap/steampipe
steampipe plugin install aws
```
-Clone:
+Steampipe will automatically use your default AWS credentials. Optionally, you can [setup multiple accounts](https://hub.steampipe.io/plugins/turbot/aws#multi-account-connections) or [customize AWS credentials](https://hub.steampipe.io/plugins/turbot/aws#configuring-aws-credentials).
-```sh
-git clone https://github.com/turbot/steampipe-mod-aws-well-architected.git
-cd steampipe-mod-aws-well-architected
-```
-
-Install mod dependencies:
+Finally, install the mod:
```sh
-steampipe mod install
+mkdir dashboards
+cd dashboards
+powerpipe mod init
+powerpipe mod install github.com/turbot/steampipe-mod-aws-well-architected
```
-### Usage
+### Browsing Dashboards
-Before running any benchmarks, it's recommended to generate your AWS credential report:
+Start Steampipe as the data source:
```sh
-aws iam generate-credential-report
+steampipe service start
```
-Start your dashboard server to get started:
+Start the dashboard server:
```sh
-steampipe dashboard
+powerpipe server
```
-By default, the dashboard interface will then be launched in a new browser
-window at http://localhost:9194. From here, you can run benchmarks by
-selecting one or searching for a specific one.
+Browse and view your dashboards at **http://localhost:9033**.
+
+### Running Checks in Your Terminal
Instead of running benchmarks in a dashboard, you can also run them within your
-terminal with the `steampipe check` command:
+terminal with the `powerpipe benchmark` command:
-Run all benchmarks:
+List available benchmarks:
```sh
-steampipe check all
+powerpipe benchmark list
```
-Run a single benchmark:
+Run a benchmark:
```sh
-steampipe check benchmark.well_architected_framework
+powerpipe benchmark run well_architected_framework
```
Run a benchmark for a specific pillar:
```sh
-steampipe check benchmark.well_architected_framework_security
+powerpipe benchmark run well_architected_framework_security
```
Run a benchmark for a specific question:
```sh
-steampipe check benchmark.well_architected_framework_sec01
+powerpipe benchmark run well_architected_framework_sec01
```
Run a benchmark for a specific best practice:
```sh
-steampipe check benchmark.well_architected_framework_sec01_bp01
+powerpipe benchmark run well_architected_framework_sec01_bp01
```
Different output formats are also available, for more information please see
-[Output Formats](https://steampipe.io/docs/reference/cli/check#output-formats).
+[Output Formats](https://powerpipe.io/docs/reference/cli/benchmark#output-formats).
-### Credentials
-
-This mod uses the credentials configured in the [Steampipe AWS plugin](https://hub.steampipe.io/plugins/turbot/aws).
+### Common and Tag Dimensions
-### Configuration
+The benchmark queries use common properties (like `account_id`, `connection_name` and `region`) and tags that are defined in the dependent [AWS Compliance mod](https://github.com/turbot/steampipe-mod-aws-compliance) These properties can be executed in the following ways:
-No extra configuration is required.
+It's easiest to setup your vars file, starting with the sample:
-### Common and Tag Dimensions
+```sh
+cp steampipe.spvars.example steampipe.spvars
+vi steampipe.spvars
+```
-The benchmark queries use common properties (like `account_id`, `connection_name` and `region`) and tags that are defined in the dependent [AWS Compliance mod](https://github.com/turbot/steampipe-mod-aws-compliance). These properties can be executed in the following ways:
+Alternatively you can pass variables on the command line:
-- Copy and rename the `steampipe.spvars.example` file to `steampipe.spvars`, and then modify the variable values inside that file
+```sh
+powerpipe benchmark run well_architected_framework_security --var 'common_dimensions=["account_id", "connection_name", "region"]'
+```
-- Pass in a value on the command line:
+Or through environment variables:
- ```shell
- steampipe check benchmark.well_architected_framework_security --var 'common_dimensions=["account_id", "connection_name", "region"]'
- ```
+```sh
+export PP_VAR_common_dimensions='["account_id", "connection_name", "region"]'
+export PP_VAR_tag_dimensions='["Environment", "Owner"]'
+powerpipe benchmark run well_architected_framework_security
+```
- ```shell
- steampipe check benchmark.well_architected_framework_security --var 'tag_dimensions=["Environment", "Owner"]'
- ```
+## Open Source & Contributing
-## Contributing
+This repository is published under the [Apache 2.0 license](https://www.apache.org/licenses/LICENSE-2.0). Please see our [code of conduct](https://github.com/turbot/.github/blob/main/CODE_OF_CONDUCT.md). We look forward to collaborating with you!
-If you have an idea for additional controls or just want to help maintain and extend this mod ([or others](https://github.com/topics/steampipe-mod)) we would love you to join the community and start contributing.
+[Steampipe](https://steampipe.io) and [Powerpipe](https://powerpipe.io) are products produced from this open source software, exclusively by [Turbot HQ, Inc](https://turbot.com). They are distributed under our commercial terms. Others are allowed to make their own distribution of the software, but cannot use any of the Turbot trademarks, cloud services, etc. You can learn more in our [Open Source FAQ](https://turbot.com/open-source).
-- **[Join #steampipe on Slack →](https://turbot.com/community/join)** and hang out with other Mod developers.
+## Get Involved
-Please see the [contribution guidelines](https://github.com/turbot/steampipe/blob/main/CONTRIBUTING.md) and our [code of conduct](https://github.com/turbot/steampipe/blob/main/CODE_OF_CONDUCT.md). All contributions are subject to the [Apache 2.0 open source license](https://github.com/turbot/steampipe-mod-aws-well-architected/blob/main/LICENSE).
+**[Join #powerpipe on Slack →](https://turbot.com/community/join)**
-Want to help but not sure where to start? Pick up one of the `help wanted` issues:
+Want to help but don't know where to start? Pick up one of the `help wanted` issues:
-- [Steampipe](https://github.com/turbot/steampipe/labels/help%20wanted)
+- [Powerpipe](https://github.com/turbot/powerpipe/labels/help%20wanted)
- [AWS Well-Architected Mod](https://github.com/turbot/steampipe-mod-aws-well-architected/labels/help%20wanted)
diff --git a/mod.sp b/mod.sp
index e1e18db..a02e1f1 100644
--- a/mod.sp
+++ b/mod.sp
@@ -1,78 +1,15 @@
-// Benchmarks and controls for specific services should override the "service" tag
-locals {
- aws_well_architected_common_tags = {
- category = "Compliance"
- plugin = "aws"
- service = "AWS"
- }
-}
-
-variable "common_dimensions" {
- type = list(string)
- description = "A list of common dimensions to add to each control."
- # Define which common dimensions should be added to each control.
- # - account_id
- # - connection_name (_ctx ->> 'connection_name')
- # - region
- default = ["account_id", "region"]
-}
-
-variable "tag_dimensions" {
- type = list(string)
- description = "A list of tags to add as dimensions to each control."
- # A list of tag names to include as dimensions for resources that support
- # tags (e.g. "Owner", "Environment"). Default to empty since tag names are
- # a personal choice - for commonly used tag names see
- # https://docs.aws.amazon.com/general/latest/gr/aws_tagging.html#tag-categories
- default = []
-}
-
-locals {
-
- # Local internal variable to build the SQL select clause for common
- # dimensions using a table name qualifier if required. Do not edit directly.
- common_dimensions_qualifier_sql = <<-EOQ
- %{~if contains(var.common_dimensions, "connection_name")}, __QUALIFIER___ctx ->> 'connection_name' as connection_name%{endif~}
- %{~if contains(var.common_dimensions, "region")}, __QUALIFIER__region%{endif~}
- %{~if contains(var.common_dimensions, "account_id")}, __QUALIFIER__account_id%{endif~}
- EOQ
-
- common_dimensions_qualifier_global_sql = <<-EOQ
- %{~if contains(var.common_dimensions, "connection_name")}, __QUALIFIER___ctx ->> 'connection_name' as connection_name%{endif~}
- %{~if contains(var.common_dimensions, "account_id")}, __QUALIFIER__account_id%{endif~}
- EOQ
-
- # Local internal variable to build the SQL select clause for tag
- # dimensions. Do not edit directly.
- tag_dimensions_qualifier_sql = <<-EOQ
- %{~for dim in var.tag_dimensions}, __QUALIFIER__tags ->> '${dim}' as "${replace(dim, "\"", "\"\"")}"%{endfor~}
- EOQ
-
-}
-
-locals {
-
- # Local internal variable with the full SQL select clause for common
- # dimensions. Do not edit directly.
- common_dimensions_sql = replace(local.common_dimensions_qualifier_sql, "__QUALIFIER__", "")
- common_dimensions_global_sql = replace(local.common_dimensions_qualifier_global_sql, "__QUALIFIER__", "")
- tag_dimensions_sql = replace(local.tag_dimensions_qualifier_sql, "__QUALIFIER__", "")
-
-}
-
-
mod "aws_well_architected" {
- # hub metadata
+ # Hub metadata
title = "AWS Well-Architected"
- description = "Run controls across all of your AWS accounts to check if they are following AWS Well-Architected best practices using Steampipe."
+ description = "Run controls across all of your AWS accounts to check if they are following AWS Well-Architected best practices using Powerpipe and Steampipe."
color = "#FF9900"
documentation = file("./docs/index.md")
icon = "/images/mods/turbot/aws-well-architected.svg"
categories = ["aws", "compliance", "public cloud", "security"]
opengraph {
- title = "Steampipe Mod for AWS Well-Architected"
- description = "Run controls across all of your AWS accounts to check if they are following AWS Well-Architected best practices using Steampipe."
+ title = "Powerpipe Mod for AWS Well-Architected"
+ description = "Run controls across all of your AWS accounts to check if they are following AWS Well-Architected best practices using Powerpipe and Steampipe."
image = "/images/mods/turbot/aws-well-architected-social-graphic.png"
}
diff --git a/variables.sp b/variables.sp
new file mode 100644
index 0000000..9e6bd6f
--- /dev/null
+++ b/variables.sp
@@ -0,0 +1,62 @@
+// Benchmarks and controls for specific services should override the "service" tag
+locals {
+ aws_well_architected_common_tags = {
+ category = "Compliance"
+ plugin = "aws"
+ service = "AWS"
+ }
+}
+
+variable "common_dimensions" {
+ type = list(string)
+ description = "A list of common dimensions to add to each control."
+ # Define which common dimensions should be added to each control.
+ # - account_id
+ # - connection_name (_ctx ->> 'connection_name')
+ # - region
+ default = ["account_id", "region"]
+}
+
+variable "tag_dimensions" {
+ type = list(string)
+ description = "A list of tags to add as dimensions to each control."
+ # A list of tag names to include as dimensions for resources that support
+ # tags (e.g. "Owner", "Environment"). Default to empty since tag names are
+ # a personal choice - for commonly used tag names see
+ # https://docs.aws.amazon.com/general/latest/gr/aws_tagging.html#tag-categories
+ default = []
+}
+
+locals {
+
+ # Local internal variable to build the SQL select clause for common
+ # dimensions using a table name qualifier if required. Do not edit directly.
+ common_dimensions_qualifier_sql = <<-EOQ
+ %{~if contains(var.common_dimensions, "connection_name")}, __QUALIFIER___ctx ->> 'connection_name' as connection_name%{endif~}
+ %{~if contains(var.common_dimensions, "region")}, __QUALIFIER__region%{endif~}
+ %{~if contains(var.common_dimensions, "account_id")}, __QUALIFIER__account_id%{endif~}
+ EOQ
+
+ common_dimensions_qualifier_global_sql = <<-EOQ
+ %{~if contains(var.common_dimensions, "connection_name")}, __QUALIFIER___ctx ->> 'connection_name' as connection_name%{endif~}
+ %{~if contains(var.common_dimensions, "account_id")}, __QUALIFIER__account_id%{endif~}
+ EOQ
+
+ # Local internal variable to build the SQL select clause for tag
+ # dimensions. Do not edit directly.
+ tag_dimensions_qualifier_sql = <<-EOQ
+ %{~for dim in var.tag_dimensions}, __QUALIFIER__tags ->> '${dim}' as "${replace(dim, "\"", "\"\"")}"%{endfor~}
+ EOQ
+
+}
+
+locals {
+
+ # Local internal variable with the full SQL select clause for common
+ # dimensions. Do not edit directly.
+ common_dimensions_sql = replace(local.common_dimensions_qualifier_sql, "__QUALIFIER__", "")
+ common_dimensions_global_sql = replace(local.common_dimensions_qualifier_global_sql, "__QUALIFIER__", "")
+ tag_dimensions_sql = replace(local.tag_dimensions_qualifier_sql, "__QUALIFIER__", "")
+
+}
+
-
-## References
-
-[AWS](https://aws.amazon.com/) provides on-demand cloud computing platforms and APIs to authenticated customers on a metered pay-as-you-go basis.
-
-[AWS Well-Architected](https://aws.amazon.com/architecture/well-architected/) helps cloud architects build secure, high-performing, resilient, and efficient infrastructure for a variety of applications and workloads.
-
-[Steampipe](https://steampipe.io) is an open source CLI to instantly query cloud APIs using SQL.
-
-[Steampipe Mods](https://steampipe.io/docs/reference/mod-resources#mod) are collections of `named queries`, and codified `controls` that can be used to test current configuration of your cloud resources against a desired configuration.
## Documentation
-- **[Benchmarks and controls →](https://hub.steampipe.io/mods/turbot/aws_well_architected/controls)**
-- **[Named queries →](https://hub.steampipe.io/mods/turbot/aws_well_architected/queries)**
+- **[Benchmarks and controls →](https://hub.powerpipe.io/mods/turbot/aws_well_architected/controls)**
+- **[Named queries →](https://hub.powerpipe.io/mods/turbot/aws_well_architected/queries)**
-## Getting started
+## Getting Started
### Installation
-Download and install Steampipe (https://steampipe.io/downloads). Or use Brew:
+Install Powerpipe (https://powerpipe.io/downloads), or use Brew:
```sh
-brew tap turbot/tap
-brew install steampipe
+brew install turbot/tap/powerpipe
```
-Install the AWS plugin with [Steampipe](https://steampipe.io):
+This mod also requires [Steampipe](https://steampipe.io) with the [AWS plugin](https://hub.steampipe.io/plugins/turbot/aws) as the data source. Install Steampipe (https://steampipe.io/downloads), or use Brew:
```sh
+brew install turbot/tap/steampipe
steampipe plugin install aws
```
-Clone:
+Steampipe will automatically use your default AWS credentials. Optionally, you can [setup multiple accounts](https://hub.steampipe.io/plugins/turbot/aws#multi-account-connections) or [customize AWS credentials](https://hub.steampipe.io/plugins/turbot/aws#configuring-aws-credentials).
-```sh
-git clone https://github.com/turbot/steampipe-mod-aws-well-architected.git
-cd steampipe-mod-aws-well-architected
-```
-
-Install mod dependencies:
+Finally, install the mod:
```sh
-steampipe mod install
+mkdir dashboards
+cd dashboards
+powerpipe mod init
+powerpipe mod install github.com/turbot/steampipe-mod-aws-well-architected
```
-### Usage
+### Browsing Dashboards
-Before running any benchmarks, it's recommended to generate your AWS credential report:
+Start Steampipe as the data source:
```sh
-aws iam generate-credential-report
+steampipe service start
```
-Start your dashboard server to get started:
+Start the dashboard server:
```sh
-steampipe dashboard
+powerpipe server
```
-By default, the dashboard interface will then be launched in a new browser
-window at http://localhost:9194. From here, you can run benchmarks by
-selecting one or searching for a specific one.
+Browse and view your dashboards at **http://localhost:9033**.
+
+### Running Checks in Your Terminal
Instead of running benchmarks in a dashboard, you can also run them within your
-terminal with the `steampipe check` command:
+terminal with the `powerpipe benchmark` command:
-Run all benchmarks:
+List available benchmarks:
```sh
-steampipe check all
+powerpipe benchmark list
```
-Run a single benchmark:
+Run a benchmark:
```sh
-steampipe check benchmark.well_architected_framework
+powerpipe benchmark run well_architected_framework
```
Run a benchmark for a specific pillar:
```sh
-steampipe check benchmark.well_architected_framework_security
+powerpipe benchmark run well_architected_framework_security
```
Run a benchmark for a specific question:
```sh
-steampipe check benchmark.well_architected_framework_sec01
+powerpipe benchmark run well_architected_framework_sec01
```
Run a benchmark for a specific best practice:
```sh
-steampipe check benchmark.well_architected_framework_sec01_bp01
+powerpipe benchmark run well_architected_framework_sec01_bp01
```
Different output formats are also available, for more information please see
-[Output Formats](https://steampipe.io/docs/reference/cli/check#output-formats).
+[Output Formats](https://powerpipe.io/docs/reference/cli/benchmark#output-formats).
-### Credentials
-
-This mod uses the credentials configured in the [Steampipe AWS plugin](https://hub.steampipe.io/plugins/turbot/aws).
+### Common and Tag Dimensions
-### Configuration
+The benchmark queries use common properties (like `account_id`, `connection_name` and `region`) and tags that are defined in the dependent [AWS Compliance mod](https://github.com/turbot/steampipe-mod-aws-compliance) These properties can be executed in the following ways:
-No extra configuration is required.
+It's easiest to setup your vars file, starting with the sample:
-### Common and Tag Dimensions
+```sh
+cp steampipe.spvars.example steampipe.spvars
+vi steampipe.spvars
+```
-The benchmark queries use common properties (like `account_id`, `connection_name` and `region`) and tags that are defined in the dependent [AWS Compliance mod](https://github.com/turbot/steampipe-mod-aws-compliance). These properties can be executed in the following ways:
+Alternatively you can pass variables on the command line:
-- Copy and rename the `steampipe.spvars.example` file to `steampipe.spvars`, and then modify the variable values inside that file
+```sh
+powerpipe benchmark run well_architected_framework_security --var 'common_dimensions=["account_id", "connection_name", "region"]'
+```
-- Pass in a value on the command line:
+Or through environment variables:
- ```shell
- steampipe check benchmark.well_architected_framework_security --var 'common_dimensions=["account_id", "connection_name", "region"]'
- ```
+```sh
+export PP_VAR_common_dimensions='["account_id", "connection_name", "region"]'
+export PP_VAR_tag_dimensions='["Environment", "Owner"]'
+powerpipe benchmark run well_architected_framework_security
+```
- ```shell
- steampipe check benchmark.well_architected_framework_security --var 'tag_dimensions=["Environment", "Owner"]'
- ```
+## Open Source & Contributing
-## Contributing
+This repository is published under the [Apache 2.0 license](https://www.apache.org/licenses/LICENSE-2.0). Please see our [code of conduct](https://github.com/turbot/.github/blob/main/CODE_OF_CONDUCT.md). We look forward to collaborating with you!
-If you have an idea for additional controls or just want to help maintain and extend this mod ([or others](https://github.com/topics/steampipe-mod)) we would love you to join the community and start contributing.
+[Steampipe](https://steampipe.io) and [Powerpipe](https://powerpipe.io) are products produced from this open source software, exclusively by [Turbot HQ, Inc](https://turbot.com). They are distributed under our commercial terms. Others are allowed to make their own distribution of the software, but cannot use any of the Turbot trademarks, cloud services, etc. You can learn more in our [Open Source FAQ](https://turbot.com/open-source).
-- **[Join #steampipe on Slack →](https://turbot.com/community/join)** and hang out with other Mod developers.
+## Get Involved
-Please see the [contribution guidelines](https://github.com/turbot/steampipe/blob/main/CONTRIBUTING.md) and our [code of conduct](https://github.com/turbot/steampipe/blob/main/CODE_OF_CONDUCT.md). All contributions are subject to the [Apache 2.0 open source license](https://github.com/turbot/steampipe-mod-aws-well-architected/blob/main/LICENSE).
+**[Join #powerpipe on Slack →](https://turbot.com/community/join)**
-Want to help but not sure where to start? Pick up one of the `help wanted` issues:
+Want to help but don't know where to start? Pick up one of the `help wanted` issues:
-- [Steampipe](https://github.com/turbot/steampipe/labels/help%20wanted)
+- [Powerpipe](https://github.com/turbot/powerpipe/labels/help%20wanted)
- [AWS Well-Architected Mod](https://github.com/turbot/steampipe-mod-aws-well-architected/labels/help%20wanted)
diff --git a/mod.sp b/mod.sp
index e1e18db..a02e1f1 100644
--- a/mod.sp
+++ b/mod.sp
@@ -1,78 +1,15 @@
-// Benchmarks and controls for specific services should override the "service" tag
-locals {
- aws_well_architected_common_tags = {
- category = "Compliance"
- plugin = "aws"
- service = "AWS"
- }
-}
-
-variable "common_dimensions" {
- type = list(string)
- description = "A list of common dimensions to add to each control."
- # Define which common dimensions should be added to each control.
- # - account_id
- # - connection_name (_ctx ->> 'connection_name')
- # - region
- default = ["account_id", "region"]
-}
-
-variable "tag_dimensions" {
- type = list(string)
- description = "A list of tags to add as dimensions to each control."
- # A list of tag names to include as dimensions for resources that support
- # tags (e.g. "Owner", "Environment"). Default to empty since tag names are
- # a personal choice - for commonly used tag names see
- # https://docs.aws.amazon.com/general/latest/gr/aws_tagging.html#tag-categories
- default = []
-}
-
-locals {
-
- # Local internal variable to build the SQL select clause for common
- # dimensions using a table name qualifier if required. Do not edit directly.
- common_dimensions_qualifier_sql = <<-EOQ
- %{~if contains(var.common_dimensions, "connection_name")}, __QUALIFIER___ctx ->> 'connection_name' as connection_name%{endif~}
- %{~if contains(var.common_dimensions, "region")}, __QUALIFIER__region%{endif~}
- %{~if contains(var.common_dimensions, "account_id")}, __QUALIFIER__account_id%{endif~}
- EOQ
-
- common_dimensions_qualifier_global_sql = <<-EOQ
- %{~if contains(var.common_dimensions, "connection_name")}, __QUALIFIER___ctx ->> 'connection_name' as connection_name%{endif~}
- %{~if contains(var.common_dimensions, "account_id")}, __QUALIFIER__account_id%{endif~}
- EOQ
-
- # Local internal variable to build the SQL select clause for tag
- # dimensions. Do not edit directly.
- tag_dimensions_qualifier_sql = <<-EOQ
- %{~for dim in var.tag_dimensions}, __QUALIFIER__tags ->> '${dim}' as "${replace(dim, "\"", "\"\"")}"%{endfor~}
- EOQ
-
-}
-
-locals {
-
- # Local internal variable with the full SQL select clause for common
- # dimensions. Do not edit directly.
- common_dimensions_sql = replace(local.common_dimensions_qualifier_sql, "__QUALIFIER__", "")
- common_dimensions_global_sql = replace(local.common_dimensions_qualifier_global_sql, "__QUALIFIER__", "")
- tag_dimensions_sql = replace(local.tag_dimensions_qualifier_sql, "__QUALIFIER__", "")
-
-}
-
-
mod "aws_well_architected" {
- # hub metadata
+ # Hub metadata
title = "AWS Well-Architected"
- description = "Run controls across all of your AWS accounts to check if they are following AWS Well-Architected best practices using Steampipe."
+ description = "Run controls across all of your AWS accounts to check if they are following AWS Well-Architected best practices using Powerpipe and Steampipe."
color = "#FF9900"
documentation = file("./docs/index.md")
icon = "/images/mods/turbot/aws-well-architected.svg"
categories = ["aws", "compliance", "public cloud", "security"]
opengraph {
- title = "Steampipe Mod for AWS Well-Architected"
- description = "Run controls across all of your AWS accounts to check if they are following AWS Well-Architected best practices using Steampipe."
+ title = "Powerpipe Mod for AWS Well-Architected"
+ description = "Run controls across all of your AWS accounts to check if they are following AWS Well-Architected best practices using Powerpipe and Steampipe."
image = "/images/mods/turbot/aws-well-architected-social-graphic.png"
}
diff --git a/variables.sp b/variables.sp
new file mode 100644
index 0000000..9e6bd6f
--- /dev/null
+++ b/variables.sp
@@ -0,0 +1,62 @@
+// Benchmarks and controls for specific services should override the "service" tag
+locals {
+ aws_well_architected_common_tags = {
+ category = "Compliance"
+ plugin = "aws"
+ service = "AWS"
+ }
+}
+
+variable "common_dimensions" {
+ type = list(string)
+ description = "A list of common dimensions to add to each control."
+ # Define which common dimensions should be added to each control.
+ # - account_id
+ # - connection_name (_ctx ->> 'connection_name')
+ # - region
+ default = ["account_id", "region"]
+}
+
+variable "tag_dimensions" {
+ type = list(string)
+ description = "A list of tags to add as dimensions to each control."
+ # A list of tag names to include as dimensions for resources that support
+ # tags (e.g. "Owner", "Environment"). Default to empty since tag names are
+ # a personal choice - for commonly used tag names see
+ # https://docs.aws.amazon.com/general/latest/gr/aws_tagging.html#tag-categories
+ default = []
+}
+
+locals {
+
+ # Local internal variable to build the SQL select clause for common
+ # dimensions using a table name qualifier if required. Do not edit directly.
+ common_dimensions_qualifier_sql = <<-EOQ
+ %{~if contains(var.common_dimensions, "connection_name")}, __QUALIFIER___ctx ->> 'connection_name' as connection_name%{endif~}
+ %{~if contains(var.common_dimensions, "region")}, __QUALIFIER__region%{endif~}
+ %{~if contains(var.common_dimensions, "account_id")}, __QUALIFIER__account_id%{endif~}
+ EOQ
+
+ common_dimensions_qualifier_global_sql = <<-EOQ
+ %{~if contains(var.common_dimensions, "connection_name")}, __QUALIFIER___ctx ->> 'connection_name' as connection_name%{endif~}
+ %{~if contains(var.common_dimensions, "account_id")}, __QUALIFIER__account_id%{endif~}
+ EOQ
+
+ # Local internal variable to build the SQL select clause for tag
+ # dimensions. Do not edit directly.
+ tag_dimensions_qualifier_sql = <<-EOQ
+ %{~for dim in var.tag_dimensions}, __QUALIFIER__tags ->> '${dim}' as "${replace(dim, "\"", "\"\"")}"%{endfor~}
+ EOQ
+
+}
+
+locals {
+
+ # Local internal variable with the full SQL select clause for common
+ # dimensions. Do not edit directly.
+ common_dimensions_sql = replace(local.common_dimensions_qualifier_sql, "__QUALIFIER__", "")
+ common_dimensions_global_sql = replace(local.common_dimensions_qualifier_global_sql, "__QUALIFIER__", "")
+ tag_dimensions_sql = replace(local.tag_dimensions_qualifier_sql, "__QUALIFIER__", "")
+
+}
+
 +
+ +
+
 -
- -
-## References
-
-[AWS](https://aws.amazon.com/) provides on-demand cloud computing platforms and APIs to authenticated customers on a metered pay-as-you-go basis.
-
-[AWS Well-Architected](https://aws.amazon.com/architecture/well-architected/) helps cloud architects build secure, high-performing, resilient, and efficient infrastructure for a variety of applications and workloads.
-
-[Steampipe](https://steampipe.io) is an open source CLI to instantly query cloud APIs using SQL.
-
-[Steampipe Mods](https://steampipe.io/docs/reference/mod-resources#mod) are collections of `named queries`, and codified `controls` that can be used to test current configuration of your cloud resources against a desired configuration.
## Documentation
-- **[Benchmarks and controls →](https://hub.steampipe.io/mods/turbot/aws_well_architected/controls)**
-- **[Named queries →](https://hub.steampipe.io/mods/turbot/aws_well_architected/queries)**
+- **[Benchmarks and controls →](https://hub.powerpipe.io/mods/turbot/aws_well_architected/controls)**
+- **[Named queries →](https://hub.powerpipe.io/mods/turbot/aws_well_architected/queries)**
-## Getting started
+## Getting Started
### Installation
-Download and install Steampipe (https://steampipe.io/downloads). Or use Brew:
+Install Powerpipe (https://powerpipe.io/downloads), or use Brew:
```sh
-brew tap turbot/tap
-brew install steampipe
+brew install turbot/tap/powerpipe
```
-Install the AWS plugin with [Steampipe](https://steampipe.io):
+This mod also requires [Steampipe](https://steampipe.io) with the [AWS plugin](https://hub.steampipe.io/plugins/turbot/aws) as the data source. Install Steampipe (https://steampipe.io/downloads), or use Brew:
```sh
+brew install turbot/tap/steampipe
steampipe plugin install aws
```
-Clone:
+Steampipe will automatically use your default AWS credentials. Optionally, you can [setup multiple accounts](https://hub.steampipe.io/plugins/turbot/aws#multi-account-connections) or [customize AWS credentials](https://hub.steampipe.io/plugins/turbot/aws#configuring-aws-credentials).
-```sh
-git clone https://github.com/turbot/steampipe-mod-aws-well-architected.git
-cd steampipe-mod-aws-well-architected
-```
-
-Install mod dependencies:
+Finally, install the mod:
```sh
-steampipe mod install
+mkdir dashboards
+cd dashboards
+powerpipe mod init
+powerpipe mod install github.com/turbot/steampipe-mod-aws-well-architected
```
-### Usage
+### Browsing Dashboards
-Before running any benchmarks, it's recommended to generate your AWS credential report:
+Start Steampipe as the data source:
```sh
-aws iam generate-credential-report
+steampipe service start
```
-Start your dashboard server to get started:
+Start the dashboard server:
```sh
-steampipe dashboard
+powerpipe server
```
-By default, the dashboard interface will then be launched in a new browser
-window at http://localhost:9194. From here, you can run benchmarks by
-selecting one or searching for a specific one.
+Browse and view your dashboards at **http://localhost:9033**.
+
+### Running Checks in Your Terminal
Instead of running benchmarks in a dashboard, you can also run them within your
-terminal with the `steampipe check` command:
+terminal with the `powerpipe benchmark` command:
-Run all benchmarks:
+List available benchmarks:
```sh
-steampipe check all
+powerpipe benchmark list
```
-Run a single benchmark:
+Run a benchmark:
```sh
-steampipe check benchmark.well_architected_framework
+powerpipe benchmark run well_architected_framework
```
Run a benchmark for a specific pillar:
```sh
-steampipe check benchmark.well_architected_framework_security
+powerpipe benchmark run well_architected_framework_security
```
Run a benchmark for a specific question:
```sh
-steampipe check benchmark.well_architected_framework_sec01
+powerpipe benchmark run well_architected_framework_sec01
```
Run a benchmark for a specific best practice:
```sh
-steampipe check benchmark.well_architected_framework_sec01_bp01
+powerpipe benchmark run well_architected_framework_sec01_bp01
```
Different output formats are also available, for more information please see
-[Output Formats](https://steampipe.io/docs/reference/cli/check#output-formats).
+[Output Formats](https://powerpipe.io/docs/reference/cli/benchmark#output-formats).
-### Credentials
-
-This mod uses the credentials configured in the [Steampipe AWS plugin](https://hub.steampipe.io/plugins/turbot/aws).
+### Common and Tag Dimensions
-### Configuration
+The benchmark queries use common properties (like `account_id`, `connection_name` and `region`) and tags that are defined in the dependent [AWS Compliance mod](https://github.com/turbot/steampipe-mod-aws-compliance) These properties can be executed in the following ways:
-No extra configuration is required.
+It's easiest to setup your vars file, starting with the sample:
-### Common and Tag Dimensions
+```sh
+cp steampipe.spvars.example steampipe.spvars
+vi steampipe.spvars
+```
-The benchmark queries use common properties (like `account_id`, `connection_name` and `region`) and tags that are defined in the dependent [AWS Compliance mod](https://github.com/turbot/steampipe-mod-aws-compliance). These properties can be executed in the following ways:
+Alternatively you can pass variables on the command line:
-- Copy and rename the `steampipe.spvars.example` file to `steampipe.spvars`, and then modify the variable values inside that file
+```sh
+powerpipe benchmark run well_architected_framework_security --var 'common_dimensions=["account_id", "connection_name", "region"]'
+```
-- Pass in a value on the command line:
+Or through environment variables:
- ```shell
- steampipe check benchmark.well_architected_framework_security --var 'common_dimensions=["account_id", "connection_name", "region"]'
- ```
+```sh
+export PP_VAR_common_dimensions='["account_id", "connection_name", "region"]'
+export PP_VAR_tag_dimensions='["Environment", "Owner"]'
+powerpipe benchmark run well_architected_framework_security
+```
- ```shell
- steampipe check benchmark.well_architected_framework_security --var 'tag_dimensions=["Environment", "Owner"]'
- ```
+## Open Source & Contributing
-## Contributing
+This repository is published under the [Apache 2.0 license](https://www.apache.org/licenses/LICENSE-2.0). Please see our [code of conduct](https://github.com/turbot/.github/blob/main/CODE_OF_CONDUCT.md). We look forward to collaborating with you!
-If you have an idea for additional controls or just want to help maintain and extend this mod ([or others](https://github.com/topics/steampipe-mod)) we would love you to join the community and start contributing.
+[Steampipe](https://steampipe.io) and [Powerpipe](https://powerpipe.io) are products produced from this open source software, exclusively by [Turbot HQ, Inc](https://turbot.com). They are distributed under our commercial terms. Others are allowed to make their own distribution of the software, but cannot use any of the Turbot trademarks, cloud services, etc. You can learn more in our [Open Source FAQ](https://turbot.com/open-source).
-- **[Join #steampipe on Slack →](https://turbot.com/community/join)** and hang out with other Mod developers.
+## Get Involved
-Please see the [contribution guidelines](https://github.com/turbot/steampipe/blob/main/CONTRIBUTING.md) and our [code of conduct](https://github.com/turbot/steampipe/blob/main/CODE_OF_CONDUCT.md). All contributions are subject to the [Apache 2.0 open source license](https://github.com/turbot/steampipe-mod-aws-well-architected/blob/main/LICENSE).
+**[Join #powerpipe on Slack →](https://turbot.com/community/join)**
-Want to help but not sure where to start? Pick up one of the `help wanted` issues:
+Want to help but don't know where to start? Pick up one of the `help wanted` issues:
-- [Steampipe](https://github.com/turbot/steampipe/labels/help%20wanted)
+- [Powerpipe](https://github.com/turbot/powerpipe/labels/help%20wanted)
- [AWS Well-Architected Mod](https://github.com/turbot/steampipe-mod-aws-well-architected/labels/help%20wanted)
diff --git a/mod.sp b/mod.sp
index e1e18db..a02e1f1 100644
--- a/mod.sp
+++ b/mod.sp
@@ -1,78 +1,15 @@
-// Benchmarks and controls for specific services should override the "service" tag
-locals {
- aws_well_architected_common_tags = {
- category = "Compliance"
- plugin = "aws"
- service = "AWS"
- }
-}
-
-variable "common_dimensions" {
- type = list(string)
- description = "A list of common dimensions to add to each control."
- # Define which common dimensions should be added to each control.
- # - account_id
- # - connection_name (_ctx ->> 'connection_name')
- # - region
- default = ["account_id", "region"]
-}
-
-variable "tag_dimensions" {
- type = list(string)
- description = "A list of tags to add as dimensions to each control."
- # A list of tag names to include as dimensions for resources that support
- # tags (e.g. "Owner", "Environment"). Default to empty since tag names are
- # a personal choice - for commonly used tag names see
- # https://docs.aws.amazon.com/general/latest/gr/aws_tagging.html#tag-categories
- default = []
-}
-
-locals {
-
- # Local internal variable to build the SQL select clause for common
- # dimensions using a table name qualifier if required. Do not edit directly.
- common_dimensions_qualifier_sql = <<-EOQ
- %{~if contains(var.common_dimensions, "connection_name")}, __QUALIFIER___ctx ->> 'connection_name' as connection_name%{endif~}
- %{~if contains(var.common_dimensions, "region")}, __QUALIFIER__region%{endif~}
- %{~if contains(var.common_dimensions, "account_id")}, __QUALIFIER__account_id%{endif~}
- EOQ
-
- common_dimensions_qualifier_global_sql = <<-EOQ
- %{~if contains(var.common_dimensions, "connection_name")}, __QUALIFIER___ctx ->> 'connection_name' as connection_name%{endif~}
- %{~if contains(var.common_dimensions, "account_id")}, __QUALIFIER__account_id%{endif~}
- EOQ
-
- # Local internal variable to build the SQL select clause for tag
- # dimensions. Do not edit directly.
- tag_dimensions_qualifier_sql = <<-EOQ
- %{~for dim in var.tag_dimensions}, __QUALIFIER__tags ->> '${dim}' as "${replace(dim, "\"", "\"\"")}"%{endfor~}
- EOQ
-
-}
-
-locals {
-
- # Local internal variable with the full SQL select clause for common
- # dimensions. Do not edit directly.
- common_dimensions_sql = replace(local.common_dimensions_qualifier_sql, "__QUALIFIER__", "")
- common_dimensions_global_sql = replace(local.common_dimensions_qualifier_global_sql, "__QUALIFIER__", "")
- tag_dimensions_sql = replace(local.tag_dimensions_qualifier_sql, "__QUALIFIER__", "")
-
-}
-
-
mod "aws_well_architected" {
- # hub metadata
+ # Hub metadata
title = "AWS Well-Architected"
- description = "Run controls across all of your AWS accounts to check if they are following AWS Well-Architected best practices using Steampipe."
+ description = "Run controls across all of your AWS accounts to check if they are following AWS Well-Architected best practices using Powerpipe and Steampipe."
color = "#FF9900"
documentation = file("./docs/index.md")
icon = "/images/mods/turbot/aws-well-architected.svg"
categories = ["aws", "compliance", "public cloud", "security"]
opengraph {
- title = "Steampipe Mod for AWS Well-Architected"
- description = "Run controls across all of your AWS accounts to check if they are following AWS Well-Architected best practices using Steampipe."
+ title = "Powerpipe Mod for AWS Well-Architected"
+ description = "Run controls across all of your AWS accounts to check if they are following AWS Well-Architected best practices using Powerpipe and Steampipe."
image = "/images/mods/turbot/aws-well-architected-social-graphic.png"
}
diff --git a/variables.sp b/variables.sp
new file mode 100644
index 0000000..9e6bd6f
--- /dev/null
+++ b/variables.sp
@@ -0,0 +1,62 @@
+// Benchmarks and controls for specific services should override the "service" tag
+locals {
+ aws_well_architected_common_tags = {
+ category = "Compliance"
+ plugin = "aws"
+ service = "AWS"
+ }
+}
+
+variable "common_dimensions" {
+ type = list(string)
+ description = "A list of common dimensions to add to each control."
+ # Define which common dimensions should be added to each control.
+ # - account_id
+ # - connection_name (_ctx ->> 'connection_name')
+ # - region
+ default = ["account_id", "region"]
+}
+
+variable "tag_dimensions" {
+ type = list(string)
+ description = "A list of tags to add as dimensions to each control."
+ # A list of tag names to include as dimensions for resources that support
+ # tags (e.g. "Owner", "Environment"). Default to empty since tag names are
+ # a personal choice - for commonly used tag names see
+ # https://docs.aws.amazon.com/general/latest/gr/aws_tagging.html#tag-categories
+ default = []
+}
+
+locals {
+
+ # Local internal variable to build the SQL select clause for common
+ # dimensions using a table name qualifier if required. Do not edit directly.
+ common_dimensions_qualifier_sql = <<-EOQ
+ %{~if contains(var.common_dimensions, "connection_name")}, __QUALIFIER___ctx ->> 'connection_name' as connection_name%{endif~}
+ %{~if contains(var.common_dimensions, "region")}, __QUALIFIER__region%{endif~}
+ %{~if contains(var.common_dimensions, "account_id")}, __QUALIFIER__account_id%{endif~}
+ EOQ
+
+ common_dimensions_qualifier_global_sql = <<-EOQ
+ %{~if contains(var.common_dimensions, "connection_name")}, __QUALIFIER___ctx ->> 'connection_name' as connection_name%{endif~}
+ %{~if contains(var.common_dimensions, "account_id")}, __QUALIFIER__account_id%{endif~}
+ EOQ
+
+ # Local internal variable to build the SQL select clause for tag
+ # dimensions. Do not edit directly.
+ tag_dimensions_qualifier_sql = <<-EOQ
+ %{~for dim in var.tag_dimensions}, __QUALIFIER__tags ->> '${dim}' as "${replace(dim, "\"", "\"\"")}"%{endfor~}
+ EOQ
+
+}
+
+locals {
+
+ # Local internal variable with the full SQL select clause for common
+ # dimensions. Do not edit directly.
+ common_dimensions_sql = replace(local.common_dimensions_qualifier_sql, "__QUALIFIER__", "")
+ common_dimensions_global_sql = replace(local.common_dimensions_qualifier_global_sql, "__QUALIFIER__", "")
+ tag_dimensions_sql = replace(local.tag_dimensions_qualifier_sql, "__QUALIFIER__", "")
+
+}
+
-
-## References
-
-[AWS](https://aws.amazon.com/) provides on-demand cloud computing platforms and APIs to authenticated customers on a metered pay-as-you-go basis.
-
-[AWS Well-Architected](https://aws.amazon.com/architecture/well-architected/) helps cloud architects build secure, high-performing, resilient, and efficient infrastructure for a variety of applications and workloads.
-
-[Steampipe](https://steampipe.io) is an open source CLI to instantly query cloud APIs using SQL.
-
-[Steampipe Mods](https://steampipe.io/docs/reference/mod-resources#mod) are collections of `named queries`, and codified `controls` that can be used to test current configuration of your cloud resources against a desired configuration.
## Documentation
-- **[Benchmarks and controls →](https://hub.steampipe.io/mods/turbot/aws_well_architected/controls)**
-- **[Named queries →](https://hub.steampipe.io/mods/turbot/aws_well_architected/queries)**
+- **[Benchmarks and controls →](https://hub.powerpipe.io/mods/turbot/aws_well_architected/controls)**
+- **[Named queries →](https://hub.powerpipe.io/mods/turbot/aws_well_architected/queries)**
-## Getting started
+## Getting Started
### Installation
-Download and install Steampipe (https://steampipe.io/downloads). Or use Brew:
+Install Powerpipe (https://powerpipe.io/downloads), or use Brew:
```sh
-brew tap turbot/tap
-brew install steampipe
+brew install turbot/tap/powerpipe
```
-Install the AWS plugin with [Steampipe](https://steampipe.io):
+This mod also requires [Steampipe](https://steampipe.io) with the [AWS plugin](https://hub.steampipe.io/plugins/turbot/aws) as the data source. Install Steampipe (https://steampipe.io/downloads), or use Brew:
```sh
+brew install turbot/tap/steampipe
steampipe plugin install aws
```
-Clone:
+Steampipe will automatically use your default AWS credentials. Optionally, you can [setup multiple accounts](https://hub.steampipe.io/plugins/turbot/aws#multi-account-connections) or [customize AWS credentials](https://hub.steampipe.io/plugins/turbot/aws#configuring-aws-credentials).
-```sh
-git clone https://github.com/turbot/steampipe-mod-aws-well-architected.git
-cd steampipe-mod-aws-well-architected
-```
-
-Install mod dependencies:
+Finally, install the mod:
```sh
-steampipe mod install
+mkdir dashboards
+cd dashboards
+powerpipe mod init
+powerpipe mod install github.com/turbot/steampipe-mod-aws-well-architected
```
-### Usage
+### Browsing Dashboards
-Before running any benchmarks, it's recommended to generate your AWS credential report:
+Start Steampipe as the data source:
```sh
-aws iam generate-credential-report
+steampipe service start
```
-Start your dashboard server to get started:
+Start the dashboard server:
```sh
-steampipe dashboard
+powerpipe server
```
-By default, the dashboard interface will then be launched in a new browser
-window at http://localhost:9194. From here, you can run benchmarks by
-selecting one or searching for a specific one.
+Browse and view your dashboards at **http://localhost:9033**.
+
+### Running Checks in Your Terminal
Instead of running benchmarks in a dashboard, you can also run them within your
-terminal with the `steampipe check` command:
+terminal with the `powerpipe benchmark` command:
-Run all benchmarks:
+List available benchmarks:
```sh
-steampipe check all
+powerpipe benchmark list
```
-Run a single benchmark:
+Run a benchmark:
```sh
-steampipe check benchmark.well_architected_framework
+powerpipe benchmark run well_architected_framework
```
Run a benchmark for a specific pillar:
```sh
-steampipe check benchmark.well_architected_framework_security
+powerpipe benchmark run well_architected_framework_security
```
Run a benchmark for a specific question:
```sh
-steampipe check benchmark.well_architected_framework_sec01
+powerpipe benchmark run well_architected_framework_sec01
```
Run a benchmark for a specific best practice:
```sh
-steampipe check benchmark.well_architected_framework_sec01_bp01
+powerpipe benchmark run well_architected_framework_sec01_bp01
```
Different output formats are also available, for more information please see
-[Output Formats](https://steampipe.io/docs/reference/cli/check#output-formats).
+[Output Formats](https://powerpipe.io/docs/reference/cli/benchmark#output-formats).
-### Credentials
-
-This mod uses the credentials configured in the [Steampipe AWS plugin](https://hub.steampipe.io/plugins/turbot/aws).
+### Common and Tag Dimensions
-### Configuration
+The benchmark queries use common properties (like `account_id`, `connection_name` and `region`) and tags that are defined in the dependent [AWS Compliance mod](https://github.com/turbot/steampipe-mod-aws-compliance) These properties can be executed in the following ways:
-No extra configuration is required.
+It's easiest to setup your vars file, starting with the sample:
-### Common and Tag Dimensions
+```sh
+cp steampipe.spvars.example steampipe.spvars
+vi steampipe.spvars
+```
-The benchmark queries use common properties (like `account_id`, `connection_name` and `region`) and tags that are defined in the dependent [AWS Compliance mod](https://github.com/turbot/steampipe-mod-aws-compliance). These properties can be executed in the following ways:
+Alternatively you can pass variables on the command line:
-- Copy and rename the `steampipe.spvars.example` file to `steampipe.spvars`, and then modify the variable values inside that file
+```sh
+powerpipe benchmark run well_architected_framework_security --var 'common_dimensions=["account_id", "connection_name", "region"]'
+```
-- Pass in a value on the command line:
+Or through environment variables:
- ```shell
- steampipe check benchmark.well_architected_framework_security --var 'common_dimensions=["account_id", "connection_name", "region"]'
- ```
+```sh
+export PP_VAR_common_dimensions='["account_id", "connection_name", "region"]'
+export PP_VAR_tag_dimensions='["Environment", "Owner"]'
+powerpipe benchmark run well_architected_framework_security
+```
- ```shell
- steampipe check benchmark.well_architected_framework_security --var 'tag_dimensions=["Environment", "Owner"]'
- ```
+## Open Source & Contributing
-## Contributing
+This repository is published under the [Apache 2.0 license](https://www.apache.org/licenses/LICENSE-2.0). Please see our [code of conduct](https://github.com/turbot/.github/blob/main/CODE_OF_CONDUCT.md). We look forward to collaborating with you!
-If you have an idea for additional controls or just want to help maintain and extend this mod ([or others](https://github.com/topics/steampipe-mod)) we would love you to join the community and start contributing.
+[Steampipe](https://steampipe.io) and [Powerpipe](https://powerpipe.io) are products produced from this open source software, exclusively by [Turbot HQ, Inc](https://turbot.com). They are distributed under our commercial terms. Others are allowed to make their own distribution of the software, but cannot use any of the Turbot trademarks, cloud services, etc. You can learn more in our [Open Source FAQ](https://turbot.com/open-source).
-- **[Join #steampipe on Slack →](https://turbot.com/community/join)** and hang out with other Mod developers.
+## Get Involved
-Please see the [contribution guidelines](https://github.com/turbot/steampipe/blob/main/CONTRIBUTING.md) and our [code of conduct](https://github.com/turbot/steampipe/blob/main/CODE_OF_CONDUCT.md). All contributions are subject to the [Apache 2.0 open source license](https://github.com/turbot/steampipe-mod-aws-well-architected/blob/main/LICENSE).
+**[Join #powerpipe on Slack →](https://turbot.com/community/join)**
-Want to help but not sure where to start? Pick up one of the `help wanted` issues:
+Want to help but don't know where to start? Pick up one of the `help wanted` issues:
-- [Steampipe](https://github.com/turbot/steampipe/labels/help%20wanted)
+- [Powerpipe](https://github.com/turbot/powerpipe/labels/help%20wanted)
- [AWS Well-Architected Mod](https://github.com/turbot/steampipe-mod-aws-well-architected/labels/help%20wanted)
diff --git a/mod.sp b/mod.sp
index e1e18db..a02e1f1 100644
--- a/mod.sp
+++ b/mod.sp
@@ -1,78 +1,15 @@
-// Benchmarks and controls for specific services should override the "service" tag
-locals {
- aws_well_architected_common_tags = {
- category = "Compliance"
- plugin = "aws"
- service = "AWS"
- }
-}
-
-variable "common_dimensions" {
- type = list(string)
- description = "A list of common dimensions to add to each control."
- # Define which common dimensions should be added to each control.
- # - account_id
- # - connection_name (_ctx ->> 'connection_name')
- # - region
- default = ["account_id", "region"]
-}
-
-variable "tag_dimensions" {
- type = list(string)
- description = "A list of tags to add as dimensions to each control."
- # A list of tag names to include as dimensions for resources that support
- # tags (e.g. "Owner", "Environment"). Default to empty since tag names are
- # a personal choice - for commonly used tag names see
- # https://docs.aws.amazon.com/general/latest/gr/aws_tagging.html#tag-categories
- default = []
-}
-
-locals {
-
- # Local internal variable to build the SQL select clause for common
- # dimensions using a table name qualifier if required. Do not edit directly.
- common_dimensions_qualifier_sql = <<-EOQ
- %{~if contains(var.common_dimensions, "connection_name")}, __QUALIFIER___ctx ->> 'connection_name' as connection_name%{endif~}
- %{~if contains(var.common_dimensions, "region")}, __QUALIFIER__region%{endif~}
- %{~if contains(var.common_dimensions, "account_id")}, __QUALIFIER__account_id%{endif~}
- EOQ
-
- common_dimensions_qualifier_global_sql = <<-EOQ
- %{~if contains(var.common_dimensions, "connection_name")}, __QUALIFIER___ctx ->> 'connection_name' as connection_name%{endif~}
- %{~if contains(var.common_dimensions, "account_id")}, __QUALIFIER__account_id%{endif~}
- EOQ
-
- # Local internal variable to build the SQL select clause for tag
- # dimensions. Do not edit directly.
- tag_dimensions_qualifier_sql = <<-EOQ
- %{~for dim in var.tag_dimensions}, __QUALIFIER__tags ->> '${dim}' as "${replace(dim, "\"", "\"\"")}"%{endfor~}
- EOQ
-
-}
-
-locals {
-
- # Local internal variable with the full SQL select clause for common
- # dimensions. Do not edit directly.
- common_dimensions_sql = replace(local.common_dimensions_qualifier_sql, "__QUALIFIER__", "")
- common_dimensions_global_sql = replace(local.common_dimensions_qualifier_global_sql, "__QUALIFIER__", "")
- tag_dimensions_sql = replace(local.tag_dimensions_qualifier_sql, "__QUALIFIER__", "")
-
-}
-
-
mod "aws_well_architected" {
- # hub metadata
+ # Hub metadata
title = "AWS Well-Architected"
- description = "Run controls across all of your AWS accounts to check if they are following AWS Well-Architected best practices using Steampipe."
+ description = "Run controls across all of your AWS accounts to check if they are following AWS Well-Architected best practices using Powerpipe and Steampipe."
color = "#FF9900"
documentation = file("./docs/index.md")
icon = "/images/mods/turbot/aws-well-architected.svg"
categories = ["aws", "compliance", "public cloud", "security"]
opengraph {
- title = "Steampipe Mod for AWS Well-Architected"
- description = "Run controls across all of your AWS accounts to check if they are following AWS Well-Architected best practices using Steampipe."
+ title = "Powerpipe Mod for AWS Well-Architected"
+ description = "Run controls across all of your AWS accounts to check if they are following AWS Well-Architected best practices using Powerpipe and Steampipe."
image = "/images/mods/turbot/aws-well-architected-social-graphic.png"
}
diff --git a/variables.sp b/variables.sp
new file mode 100644
index 0000000..9e6bd6f
--- /dev/null
+++ b/variables.sp
@@ -0,0 +1,62 @@
+// Benchmarks and controls for specific services should override the "service" tag
+locals {
+ aws_well_architected_common_tags = {
+ category = "Compliance"
+ plugin = "aws"
+ service = "AWS"
+ }
+}
+
+variable "common_dimensions" {
+ type = list(string)
+ description = "A list of common dimensions to add to each control."
+ # Define which common dimensions should be added to each control.
+ # - account_id
+ # - connection_name (_ctx ->> 'connection_name')
+ # - region
+ default = ["account_id", "region"]
+}
+
+variable "tag_dimensions" {
+ type = list(string)
+ description = "A list of tags to add as dimensions to each control."
+ # A list of tag names to include as dimensions for resources that support
+ # tags (e.g. "Owner", "Environment"). Default to empty since tag names are
+ # a personal choice - for commonly used tag names see
+ # https://docs.aws.amazon.com/general/latest/gr/aws_tagging.html#tag-categories
+ default = []
+}
+
+locals {
+
+ # Local internal variable to build the SQL select clause for common
+ # dimensions using a table name qualifier if required. Do not edit directly.
+ common_dimensions_qualifier_sql = <<-EOQ
+ %{~if contains(var.common_dimensions, "connection_name")}, __QUALIFIER___ctx ->> 'connection_name' as connection_name%{endif~}
+ %{~if contains(var.common_dimensions, "region")}, __QUALIFIER__region%{endif~}
+ %{~if contains(var.common_dimensions, "account_id")}, __QUALIFIER__account_id%{endif~}
+ EOQ
+
+ common_dimensions_qualifier_global_sql = <<-EOQ
+ %{~if contains(var.common_dimensions, "connection_name")}, __QUALIFIER___ctx ->> 'connection_name' as connection_name%{endif~}
+ %{~if contains(var.common_dimensions, "account_id")}, __QUALIFIER__account_id%{endif~}
+ EOQ
+
+ # Local internal variable to build the SQL select clause for tag
+ # dimensions. Do not edit directly.
+ tag_dimensions_qualifier_sql = <<-EOQ
+ %{~for dim in var.tag_dimensions}, __QUALIFIER__tags ->> '${dim}' as "${replace(dim, "\"", "\"\"")}"%{endfor~}
+ EOQ
+
+}
+
+locals {
+
+ # Local internal variable with the full SQL select clause for common
+ # dimensions. Do not edit directly.
+ common_dimensions_sql = replace(local.common_dimensions_qualifier_sql, "__QUALIFIER__", "")
+ common_dimensions_global_sql = replace(local.common_dimensions_qualifier_global_sql, "__QUALIFIER__", "")
+ tag_dimensions_sql = replace(local.tag_dimensions_qualifier_sql, "__QUALIFIER__", "")
+
+}
+