When analyzing malware or 3rd party software, it's challenging to identify statically linked libraries and to understand what a function from the library is doing.
idenLib.exe is a tool for generating library signatures from .lib files.
idenLib.dp32 is a x32dbg plugin to identify library functions.
idenLib.py is an IDA Pro plugin to identify library functions.
Any feedback is greatly appreciated: @_qaz_qaz
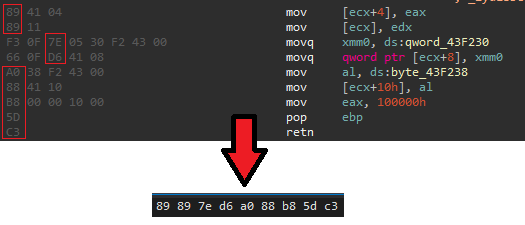
- Parse input file(
.libfile) to get a list of function addresses and function names. - Get the last opcode from each instruction and generate
MD5hash from it (you can change the hashing algorithm).
- Save the signature under the
SymExdirectory, if the input filename iszlib.lib, the output will bezlib.lib.sig, ifzlib.lib.sigalready exists under theSymExdirectory from a previous execution or from the previous version of the library, the next execution will append different signatures. If you executeidenLib.exeseveral times with different version of the.libfile, the.sigfile will include all unique function signatures.
Signature file format:
hash function_name
- Copy
SymExdirectory underx32dbg/IDA Pro's main directory - Apply signatures:
x32dbg:
IDAPro:
Only x86 is supported (adding x64 should be trivial).
- Detailed information about
C Run-Time Libraries (CRT);